Having already presented what Continuous Business Monitoring actually is, the benefits it provides for individual participants and having identified the drivers for its implementation, in this article, I will now present its different components, a procedure for its implementation and some examples of applications.
Did you miss the first part of the two-part series? No problem. Simply follow this link to the article:
Continuous Business Monitoring: An Approach to Enterprise Monitoring
Components of Continuous Business Monitoring
In what follows, I will present the possible components of CBM. Particular attention is paid to aspects related to compliance, rather than performance-related aspects, as performance indicators are more dependent on the business model and industry than compliance requirements. From the point of view of the control and monitoring system, it is possible to formulate various questions in conjunction with the use of ERP systems that support business processes (for components of the internal control system, see also: [ID06 R 211, p. 2000]). Since CBM is based on the existing structured information content of the ERP systems used by the company, the following data sets can be used for continuous monitoring on the basis of the questions mentioned above:
| Control system requirement | Data set to be continuously monitored |
| How is it ensured that business transactions are carried out with sufficient division of labor and that the principle of dual control is always adhered to (Segregation of Duties) [HeTa07][ID06, R 229, p. 2004]? | Access rights of all system users, authorization roles |
| How is it ensured that the system fundamentally handles business processes as planned and with integrity? | System settings (Customizing) with reference to the internal control system (known as “application controls”) [ID06, R 231, p. 2005]; [FA02, subsection 95]. These system settings control the process flow in the system. |
| How is it ensured that actual business transactions comply with the company’s policies and guidelines and that extraordinary business transactions are noted and tracked? | Transaction documents:Posting documents in Accounting, Purchasing, Asset documents, Sales documents |
Table 1: Control system requirements and relevant data sets
The control system requirements include both preventive and detective measures. The result is a “three-pillar system” describing the components of CBM: 1. Access rights & Segregation of Duties (preventive), 2. Application controls (preventive), 3. Analysis of business transactions (detective). The three pillars are each explained in greater detail below. The examples presented here were developed during a project with a large DAX mandate.
Procedure and phase model
To implement a CBM for all these objects of analysis, you need a procedure that is structured into phases. The figure below shows a possible procedure [WoGe09] for doing this.
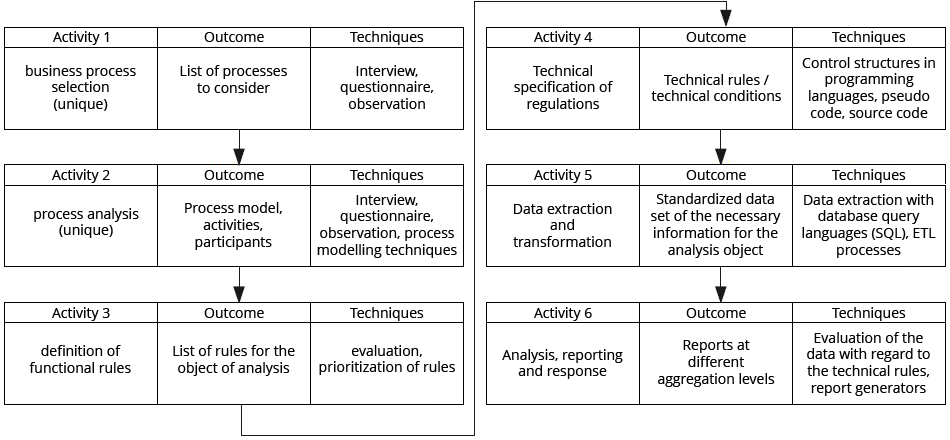
Figure 1: Procedure for implementing CBM
The continuous monitoring of the objects of analysis can be broken down into six activity phases. Please note that activities one to four are one-off activities that are required for implementation. Activities five and six are repeated continuously and on a periodic basis (e. g. daily or weekly) and are thus representative of the nature of continuous monitoring.
Activities one and two (Business Process Selection and Process Analysis) determine which business processes (for example, purchasing, sales, accounting, system administration) are to be included in continuous monitoring. This should be done on the basis of risk considerations. Once the selection has been made, the process flows must be examined and the individual process steps within the process must be identified. Activities one and two are not explained in what follows for each of the subjects of analysis, as they are elements which are common to each activity. Activities three to six are examined and explained in more detail below for each of the subjects of analysis.

Continuous monitoring of access rights and segregation of duties
The purpose of segregation of duties is to comply with the four-eye principle. This is to ensure that a business process or several steps of a business process for which work is divided up are not carried out by the same person, in order to minimize the possibility of errors and fraudulent actions ([PS06, pt. 52]; for the importance of white-collar crime in companies, see also: [PW07]). For an analysis of the access options, the user authorizations must be examined with regard to segregation of duties violations. For continuous monitoring of these authorizations, the authorization data must be continuously extracted from the system (data export) and analyzed in an evaluation logic, usually using external special analysis software. For the analysis of authorizations with regard to segregation of duties violations, standard software such as Virsa for SAP, Approva or Security Weaver (for an overview of Compliance software in the area of segregation of duties, see also [Ga08]). However, the use of this special software requires considerable effort to be put into configuration in order to meet the specific requirements of the company. The following section explains how continuous monitoring of segregation of duties can be carried out.
Activity 3 (Functional Definition of the Segregation of Duties Matrix) defines when a segregation of duties conflict exists. For this purpose, the process steps identified in activity 2 are compared with each other and then it is decided whether a segregation of duties conflict exists if both process steps can be carried out by one person. This results in a control matrix, which defines the segregation of duties violations by combining two process steps. Relevant process steps are, for example, “Supplier Data Management”, “Processing Incoming Bills” or “Outbound Payment Processing”. A segregation of duties conflict arises whenever a risk is conceivable by combining the process steps into one source. At this level, the technical details of the ERP systems used are not yet covered. The following table shows typical examples of typical segregation of duties conflicts for purchasing.
| Segregation of duties conflicts & risk |
| “Supplier Data Management” against “Processing Incoming Bills”: The user could manipulate vendor master data (for example, bank details), create a corresponding vendor invoice and thus remove funds from the company. |
| “Processing Incoming Bills” against “Outbound Payment Processing”: Payments could be made in respect of fake invoices. |
| “Supplier Data Management” against “Outbound Payment Processing”: The user could manipulate vendor master data (for example, bank details) and transfer funds to incorrect bank accounts in the payment run. |
Table 2: Examples for Segregation of Duties conflicts
In addition to defining the conflicts themselves, it would be conceivable to assign a risk score (e. g. from 1 – 10) to each conflict in order to take the severity of risks arising from segregation of duties conflicts into account.
In activity 4 (Technical Specification of the Rule Matrix), the functional set of rules is technically adjusted to the ERP system used. The individual programs of the ERP software (the transactions in SAP, for example,) must be assigned to the business process steps of the control matrix, to the extent that they are relevant. As a rule, several programs of the software are assigned to one process step, since there are always alternative or redundant functions for the same process step.
In activity 5 (Data Extraction), the users and user authorizations are first extracted from the source system and transferred to the analysis software. In activity 6 (Segregation of Duties Analysis), the technical rule matrix is applied to the extracted data and segregation of duties violations are detected. This activity also includes representations of the findings of the analysis and the corresponding responses to reduce conflicts. Various alternative ways of presentation are possible here, depending on the function of the addressee of the information. At the top level and for comparison of the status of different (subsidiary) companies, the key figures “Number of violations” and “Average number of violations per affected user” can be calculated (Figure 2). In a coordinate system, the status of various (subsidiary) companies or organizational units can then be compared (benchmarking). Improvements in the resolution of segregation of duty conflicts over time can also be displayed as pathways.
In continuous repetition of analysis and correction due to continuous monitoring, the system becomes increasingly free of segregation of duties conflicts. Small organizational units regularly have problems in expanding their division of labor in order to avoid conflicts. In this case, a procedure should be established for well-founded applications for exceptions. Exceptions should be compensated for by alternative control measures to close the control gap in the authorization system (compensatory controls).
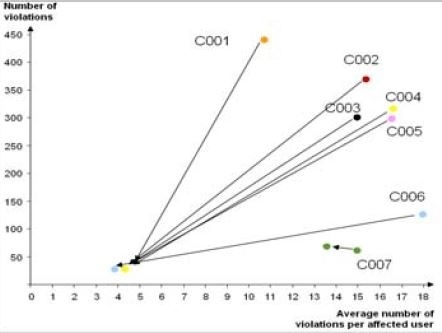
Figure 2: Representation of segregation of duties conflicts of
different units at two different points in time
With the segregation of duties conflicts, I have provided you with an example of the design of a CBM, and thus of preventive control. In addition to preventive controls for investigating segregation of duties conflicts, an application control is also conceivable. The CBM design process for these controls is identical. Activity 3 (Functional Definition of Relevant Application Controls) includes a function-specific selection of system settings with relevant reference to the Internal Control System. The following table shows possible system settings for an SAP System, for example.
| Business process | Application control | System setting with reference to the internal control system |
| System administration | Password rule | Password length must be long enough and must be changed periodically. |
| System administration | Logging | All changes to accounting master data must be logged. |
| Purchasing | Duplicate incoming invoices | The system must be set up in such a way that when you enter incoming invoices, the system checks whether this invoice has already been entered. |
| Purchasing | Logistics orders | If goods are ordered in the system, the system expects a goods receipt and an invoice receipt based on the purchase order. These operations must be linked together with each other in the system by the employee. |
| Purchasing | Tolerance values for orders | When a goods order is placed, the system automatically monitors upon receipt of goods or receipt of invoice that not too much or too little has been delivered in terms of quantity or settled in terms of price. |
Table 3: Sample system settings with relevance to the
internal control system (known as “application controls”) – Functional View
In the scientific paper (in German) entitled “Zur Automatisierung von Revisionsdienstleistungen zwecks Unternehmensüberwachung – Ein Überblick “, you will find further examples, for instance of the continuous monitoring of business transactions and processes (detective control). The paper is only available in German language and for download by following the link:

Overall view of the monitoring system
A presentation of results for individual sub-areas is not always sufficient. Addressees such as high-level decision-makers and the Supervisory Board require a highly-aggregated presentation of all sub-areas. An overall assessment must be carried out in order to assess the status of the company’s monitoring system as quickly as possible. A scoring model is suitable for this purpose, and this should be one which adds all the individual results together appropriately, so that a percentage value can be obtained for each defined level of aggregation.
The following 7 levels are suitable as levels of aggregation: 1. Group, 2. Division, 3. Subsidiaries, 4. Business Process, 5. Risk, 6. Control objective, 7. Control measure. Behind each control measure (lowest level), there is an evaluation logic that uses a scoring model to evaluate the technical specification of the control measure. The levels of aggregation add together all points for the level and calculate a percentage value. It is the responsibility of management to determine the measures to be taken if certain thresholds are not met.
Conclusion
This post has demonstrated the possible ways in which broadly automated company monitoring can be carried out within the framework of a continuous business monitoring concept. Due to the growing use of information technology and, above all, the closer integration of information systems, the automation of monitoring functions within the company is becoming an increasingly attractive proposition. Better structure and faster availability of corporate monitoring results are becoming more and more necessary, not least due to the ever-increasing number of organizations active on global markets and the higher levels of publicity due to economic crises, for example. Supervisory boards in particular must find ways of fulfilling their legal control function and should therefore take a close interest in setting up adequate monitoring measures.
If you want to know how to implement such a system, please contact us. With our advanced data extraction capacities, it is no problem for us to implement a CBM system on your behalf.
First published in: Gehrke, N.: Zur Automatisierung von Revisionsdienstleistungen zwecks Unternehmensüberwachung – Ein Überblick, Lecture Notes in Informatics, Proceedings der Jahrestagung Informatik 2009, Lübeck, 2009
Sources:
[FA02] Institut der Wirtschaftsprüfer Stellungnahmen, Grundsätze ordnungsmäßiger Buchführung bei Einsatz von Informationstechnologie, IDW RS FAIT 1, 2002.
[Ga08] Gartner Research: MarketScope for Segregation of Duty Controls within ERP and Financial Applications, 2008.
[HeTa07] Hendrawirawan, D.; Tanriverdi, H.; Zetterlund, C.; Hakam, H.; Kim, H.; Paik, H: ERP Security and Segregation of Duties Audit: A Framework for Building an Automated Solution, Information Systems Control Journal, Vol. 2, 2007.
[ID06] Institut der Wirtschaftsprüfer, Wirtschaftsprüferhandbuch 2006 Volume I, 2006.
[PS06] Institut der Wirtschaftsprüfer, PS 261: Feststellung und Beurteilung von Fehlerrisiken und Reaktionen des Abschlussprüfers auf die beurteilten Fehlerrisiken, Version as at: Sept. 6, 2006, 2006.
[PW07] PricewaterhouseCoopers: Economic crime: people, culture and controls – The 4th biennial Global Economic Crime Survey, 2007.
[WoGe09] Wolf, P.; Gehrke, N.: Continuous Compliance Monitoring in ERP Systems – A Method for Identifying Segregation of Duties Conflicts, Proceedings Konferenz Wirtschaftsinformatik, Vienna, 2009.
